Two years ago I wrote regarding Dual Firewall DMZ design. While (I hope) it does well to illustrate how a DMZ can operate, admittedly its a clumsy design and not one I’d recommend. First and foremost, DMZ design has to meet the needs of implementation; there is no one-size-fits-all solution. That said, I want to share a design that makes a great starting point.
Internal Firewall DMZ
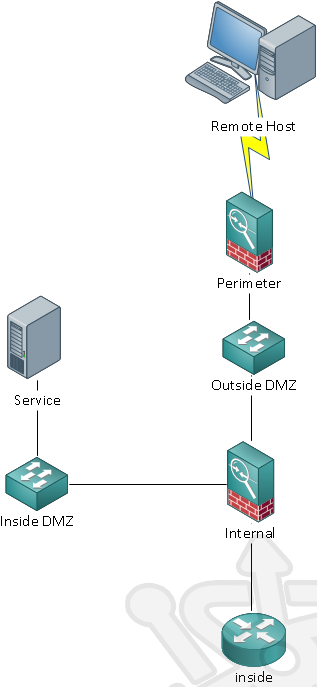
The design that follows could best be described as an Internal Firewall DMZ. The service is logically connected to the internal firewall and physically isolated from the perimeter firewall.
Security
Using our design, external traffic needs to traverse two firewalls before reaching the desired service. Its often recommended to use firewalls from different manufacturers for the external and internal security devices. In practice that’s not always possible and I would opt to have the less sophisticated firewall on the external network. It will serve as basic stateful filter ensuring that internet traffic only reaches the IPs and ports they are allowed. This will cut down on the noise the internal firewall needs to handle. The more advanced internal firewall can then provide additional threat protection through Deep Packet Inspection.
Simplicity
Between our two firewalls the external traffic rule set should be largely the same. When boiled down all external traffic will be travelling from the outside interface to DMZ interface. With the internal firewall managing the routing between internal and external traffic the service host does not require any special knowledge of the network topology. And of course traffic coming from the internal network only needs to travel between the inside and DMZ interfaces of the internal firewall.
Flexibility
Due to the simple nature of the design, we can easily scale up and add more devices on our inside DMZ with rule sets to mirror our existing service. We can even create additional internal DMZes using another internal firewall interface.